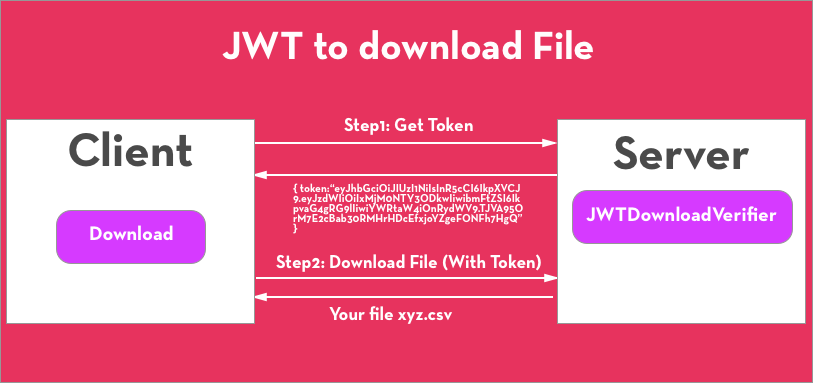
How to log out when using JWT. One does not simply log out when using… | by Arpy Vanyan | devgorilla | Medium
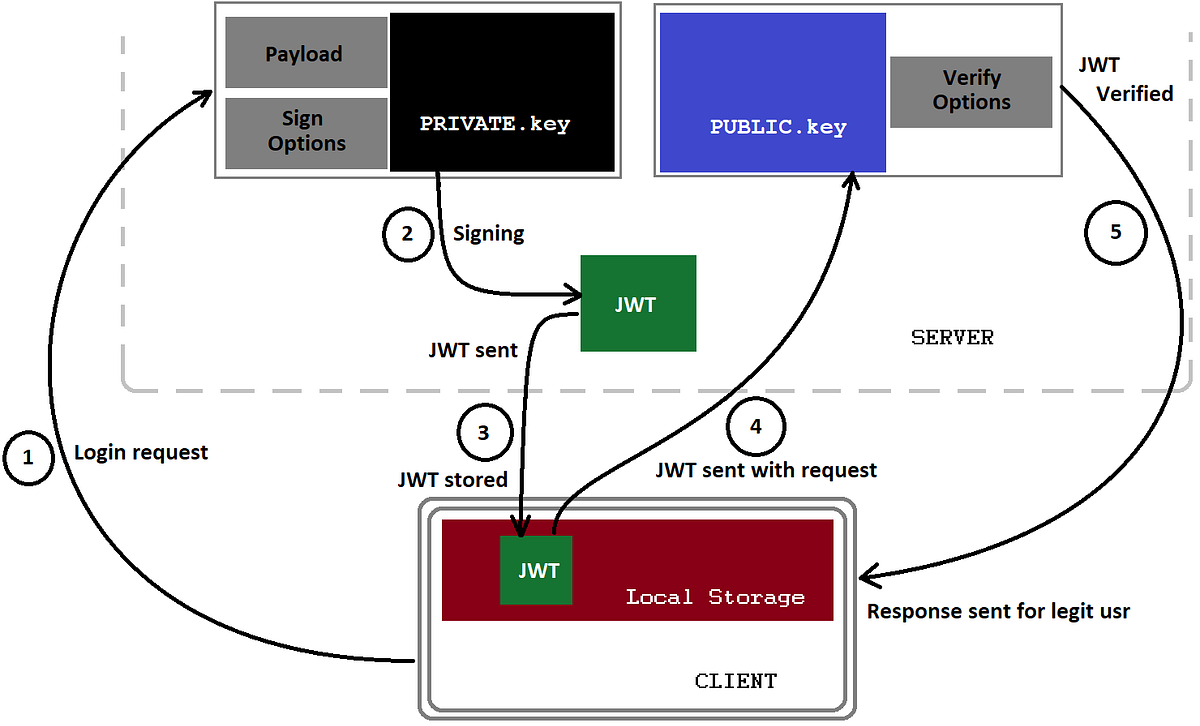
JSON Web Token (JWT) — The right way of implementing, with Node.js | by Siddhartha Chowdhury | Medium

How to Sign-In with Google in Angular and use JWT based .NET Core API Authentication (RSA) | by Christian Zink | Level Up Coding
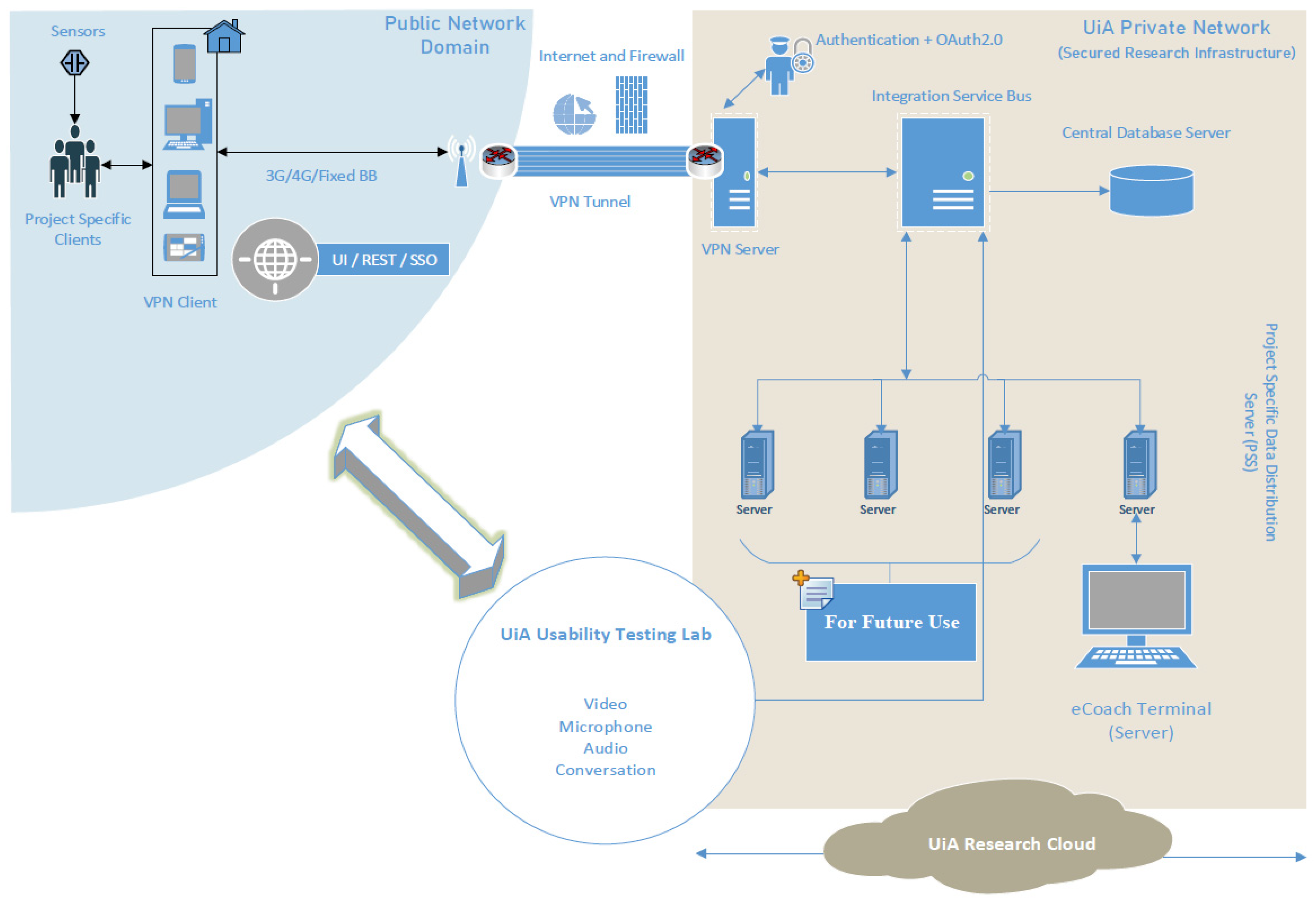
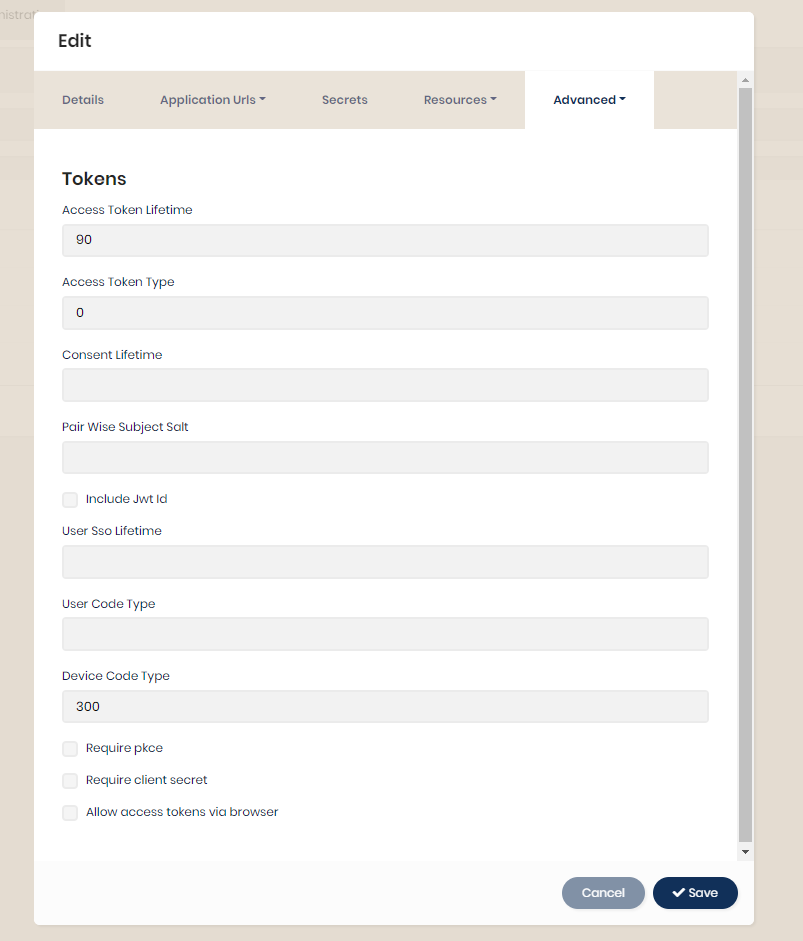
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study | HTML
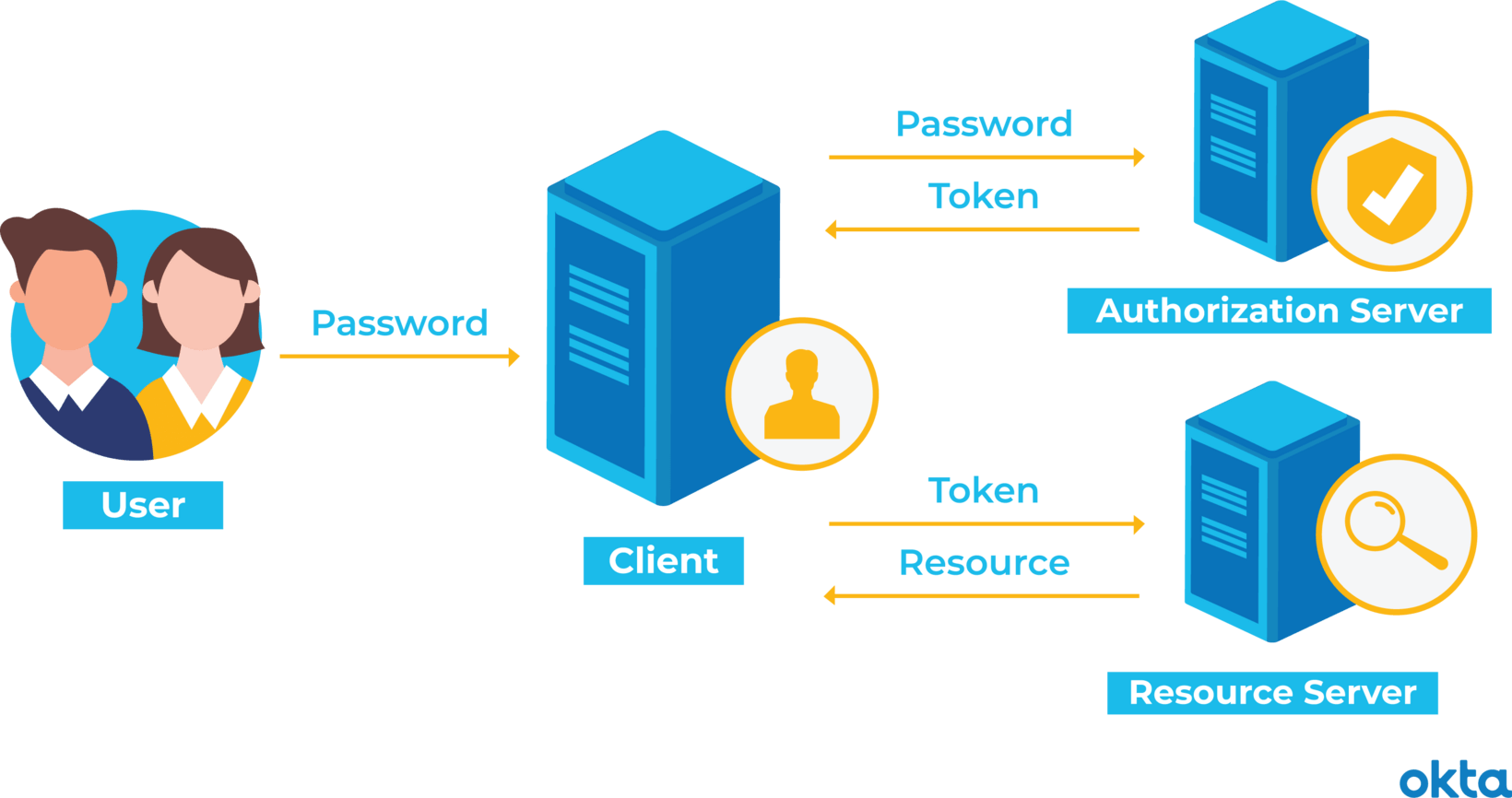
![4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book] 4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book]](https://www.oreilly.com/api/v2/epubs/9781491937006/files/assets/idds_0402.png)
4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book]
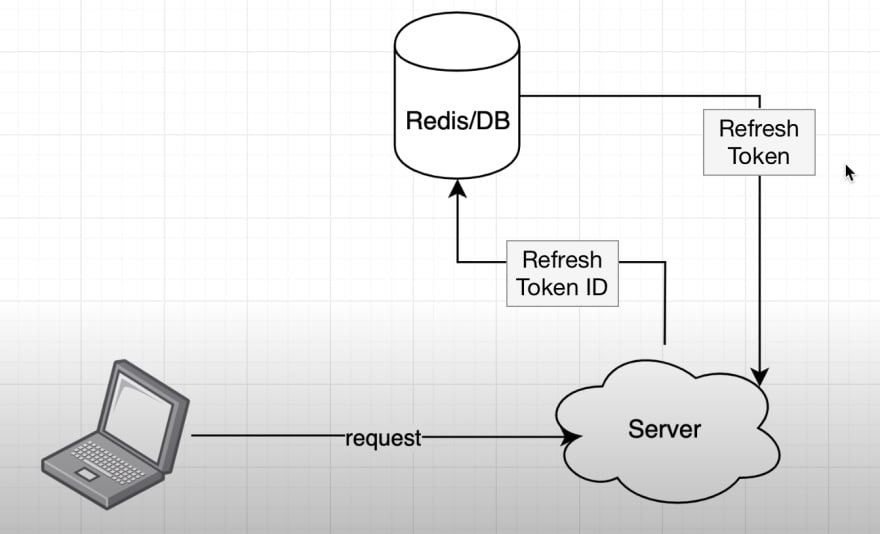
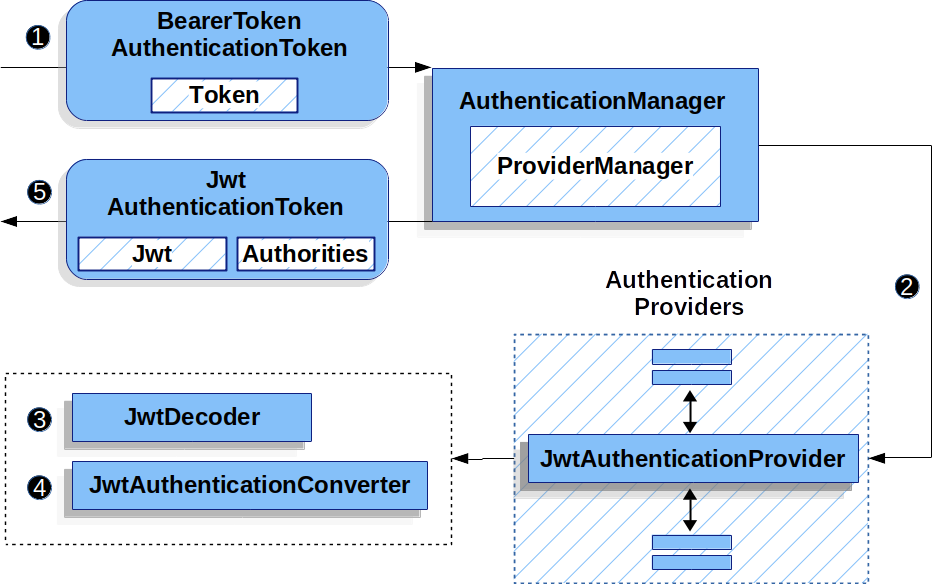
JSON web tokens are NOT meant for authenticating the same user repeatedly: Use session tokens instead - DEV Community 👩💻👨💻