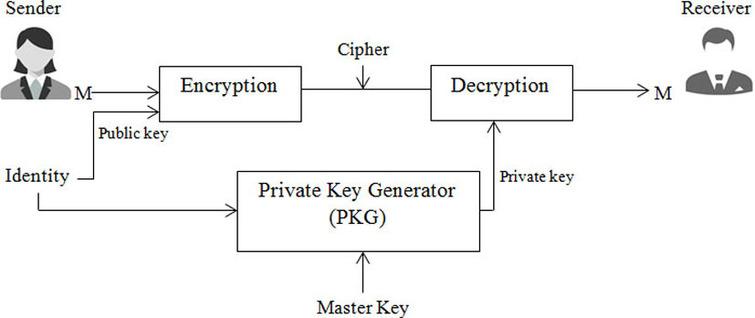
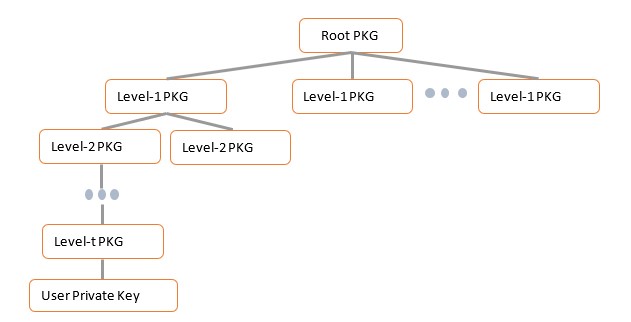
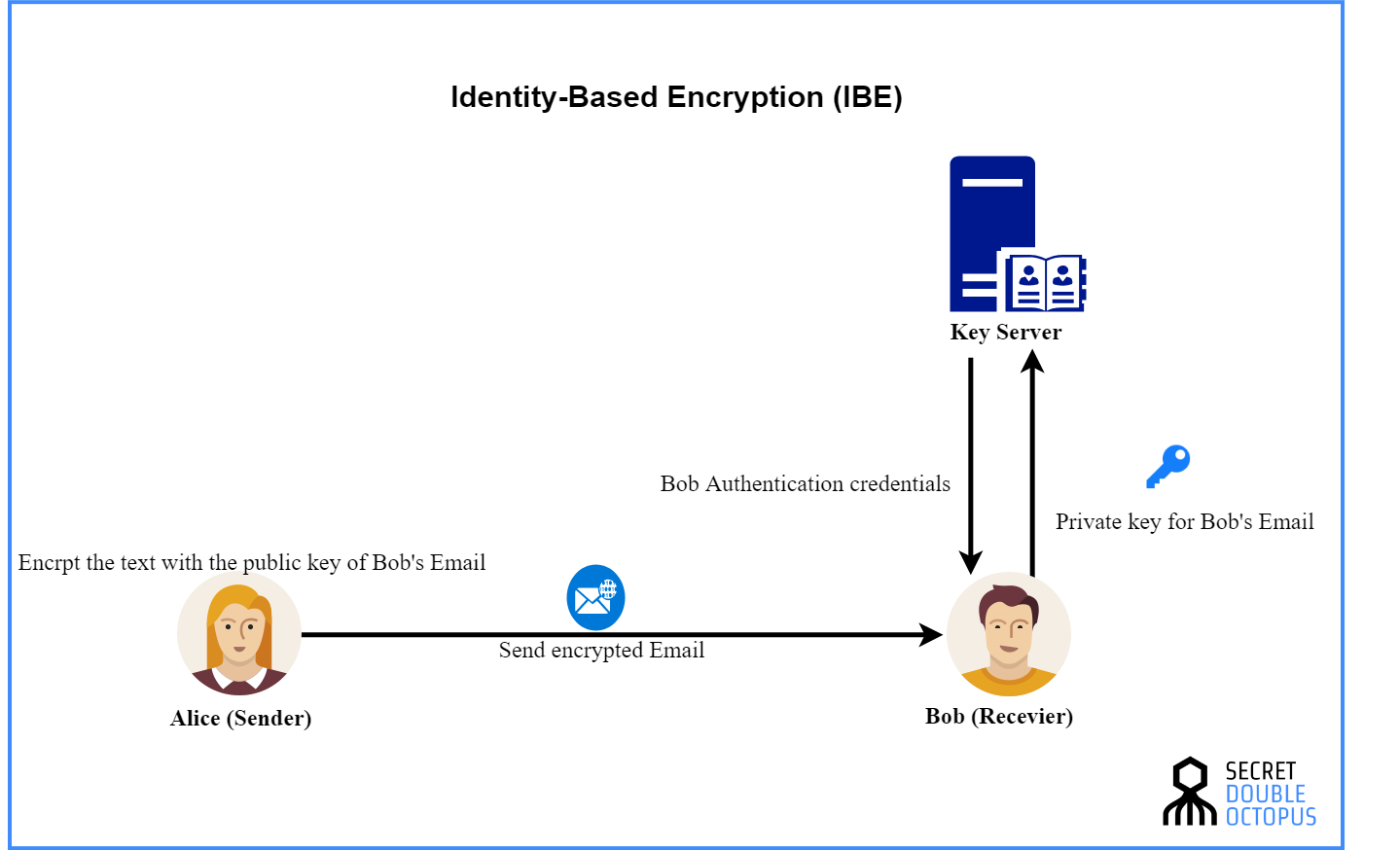
Generates private key and decrypts the received encrypted information... | Download Scientific Diagram

A New Method IBE Interfaced with Private Key Generation and Public Key Infrastructure to Achieve High Data Security | Semantic Scholar
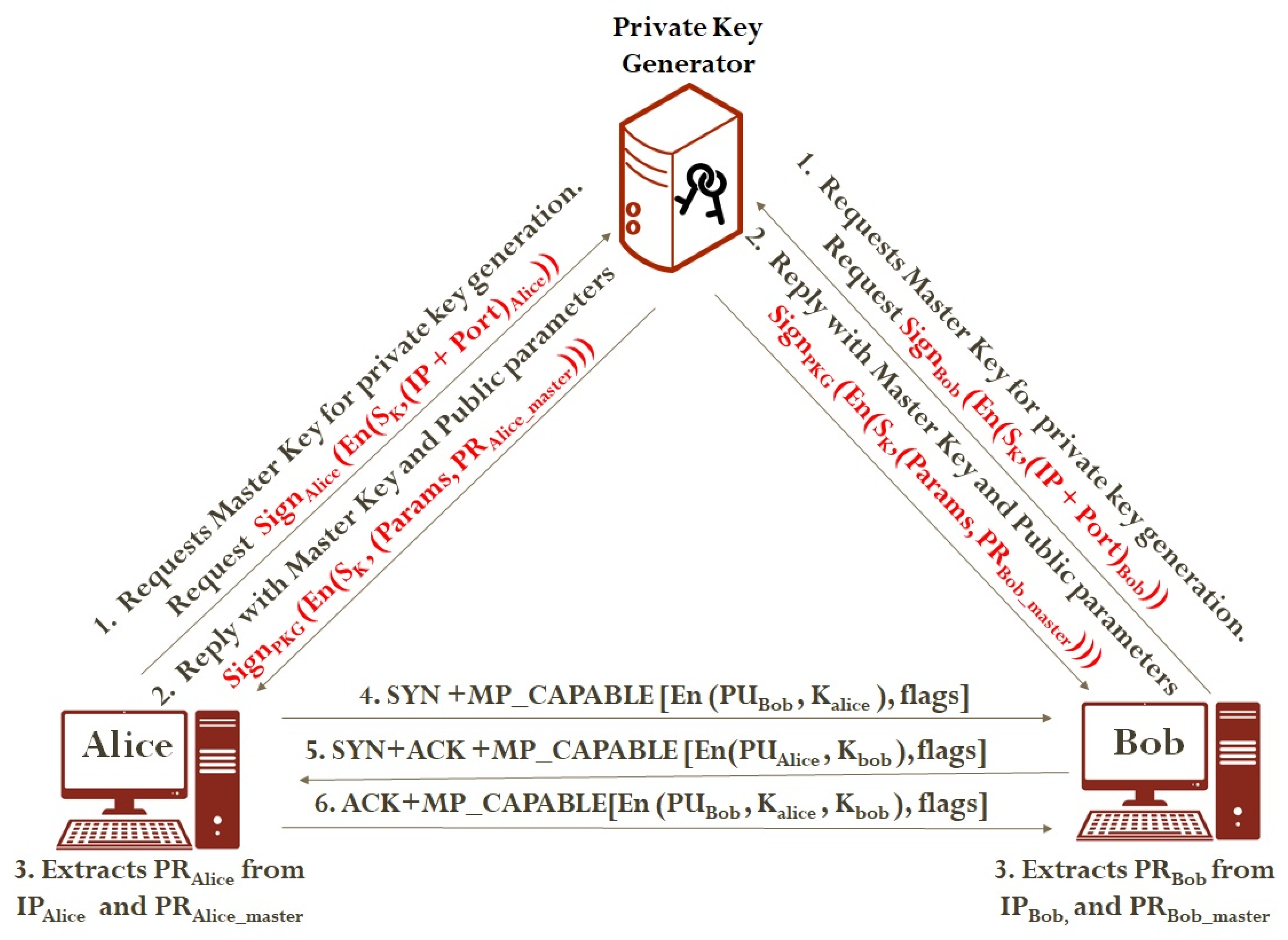
Applied Sciences | Free Full-Text | Efficient Key Exchange Using Identity-Based Encryption in Multipath TCP Environment | HTML

A New Method IBE Interfaced with Private Key Generation and Public Key Infrastructure to Achieve High Data Security | Semantic Scholar



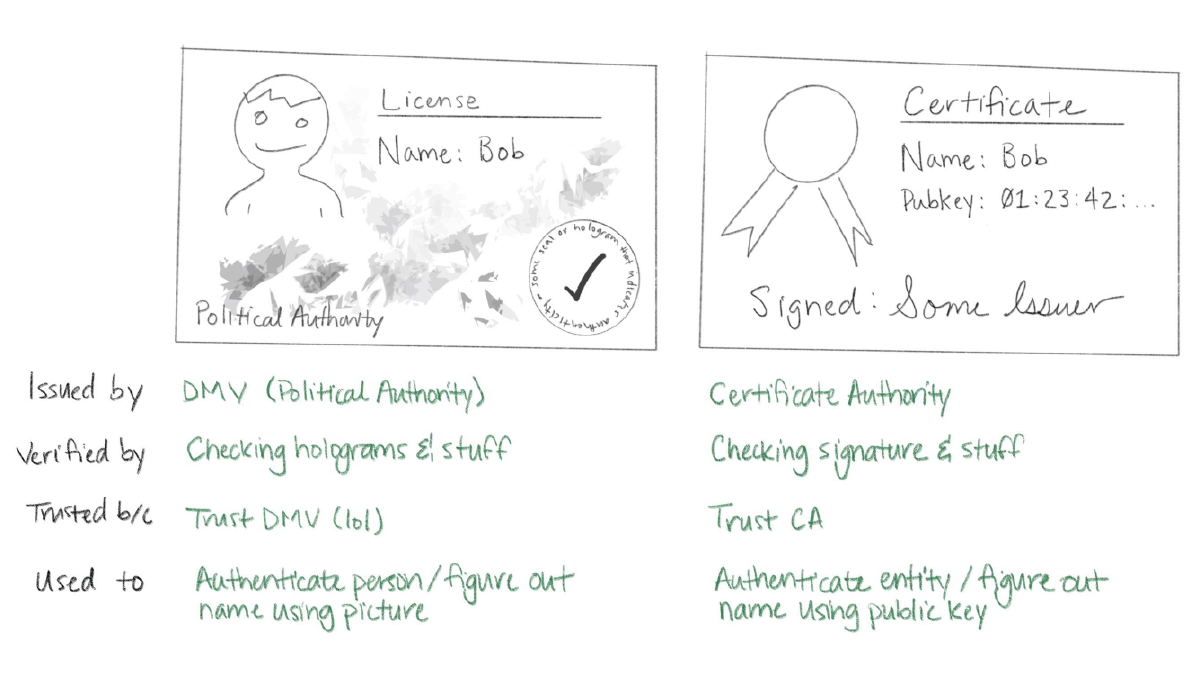






![4. Keys, Addresses, Wallets - Mastering Bitcoin [Book] 4. Keys, Addresses, Wallets - Mastering Bitcoin [Book]](https://www.oreilly.com/api/v2/epubs/9781491902639/files/images/msbt_0410.png)