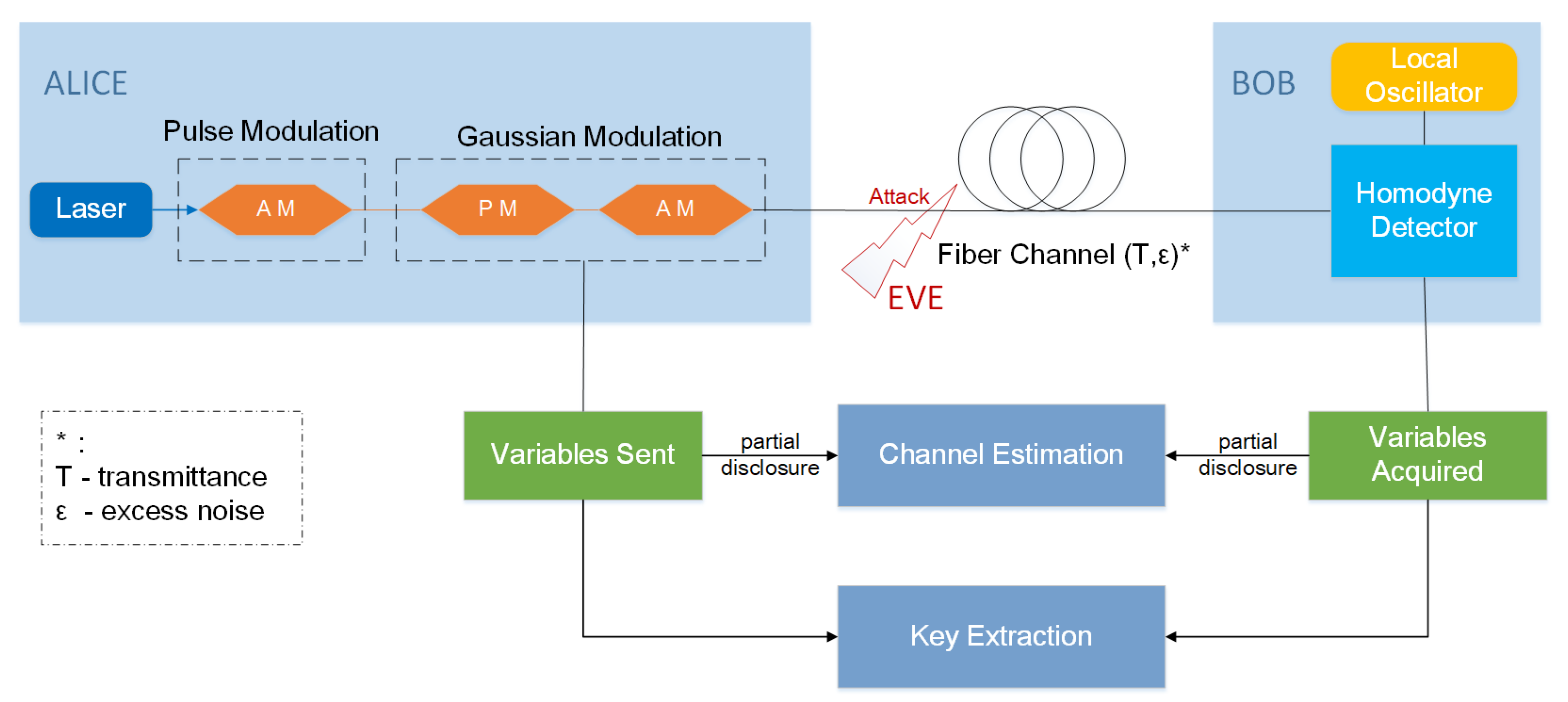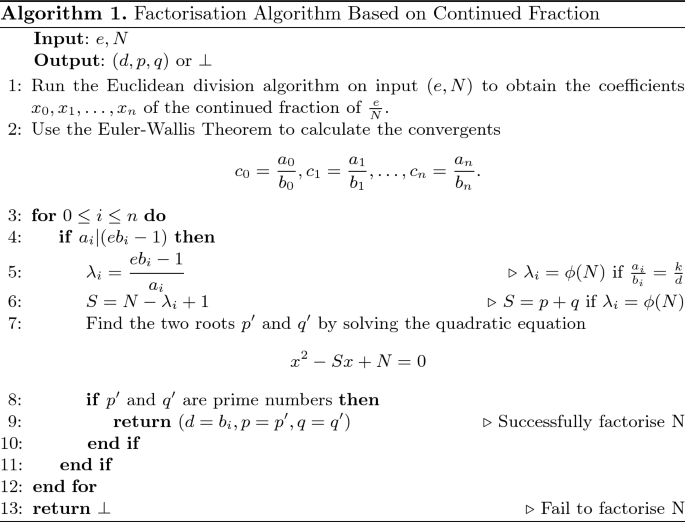
Symmetry | Free Full-Text | Small Private Exponent Attacks on RSA Using Continued Fractions and Multicore Systems

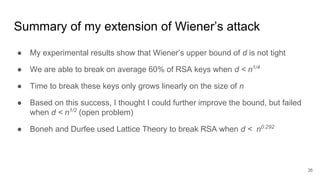
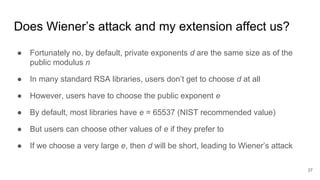
CTF Generator: Low private exponent (d) in RSA … the Wiener attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

CTF Generator: Low private exponent (d) in RSA … the Wiener attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
GitHub - pablocelayes/rsa-wiener-attack: A Python implementation of the Wiener attack on RSA public-key encryption scheme.