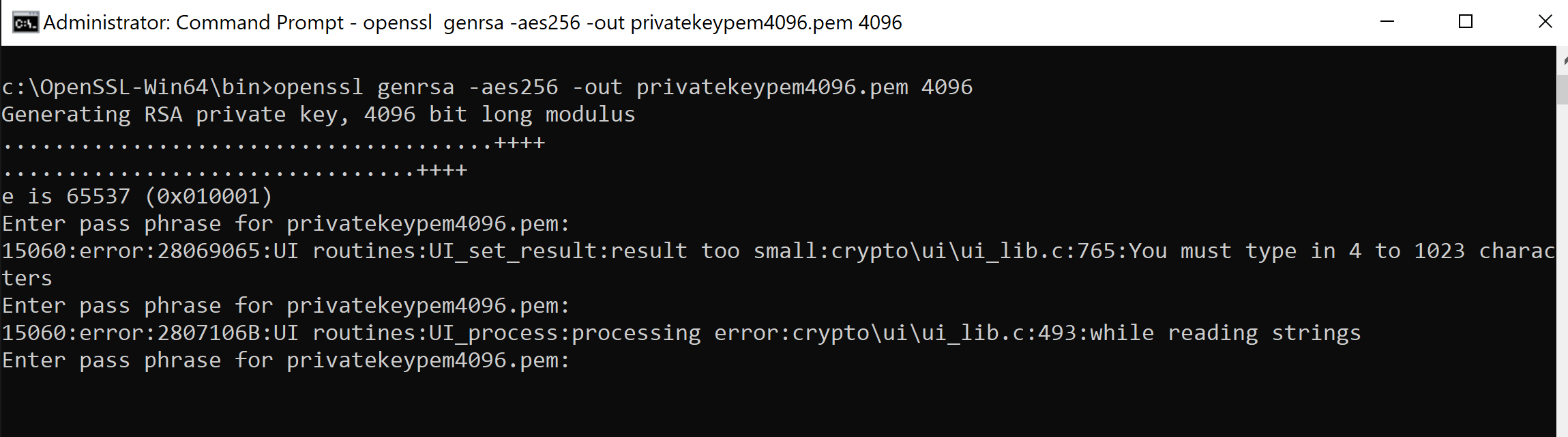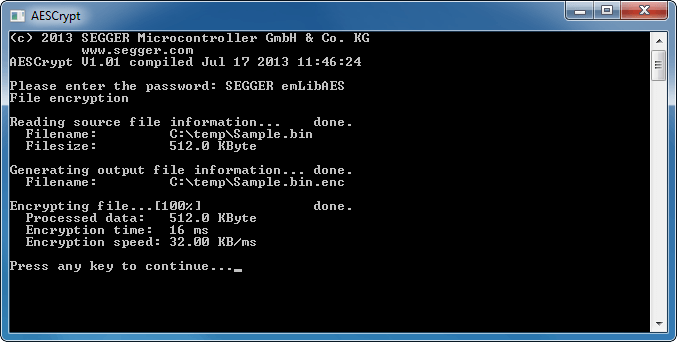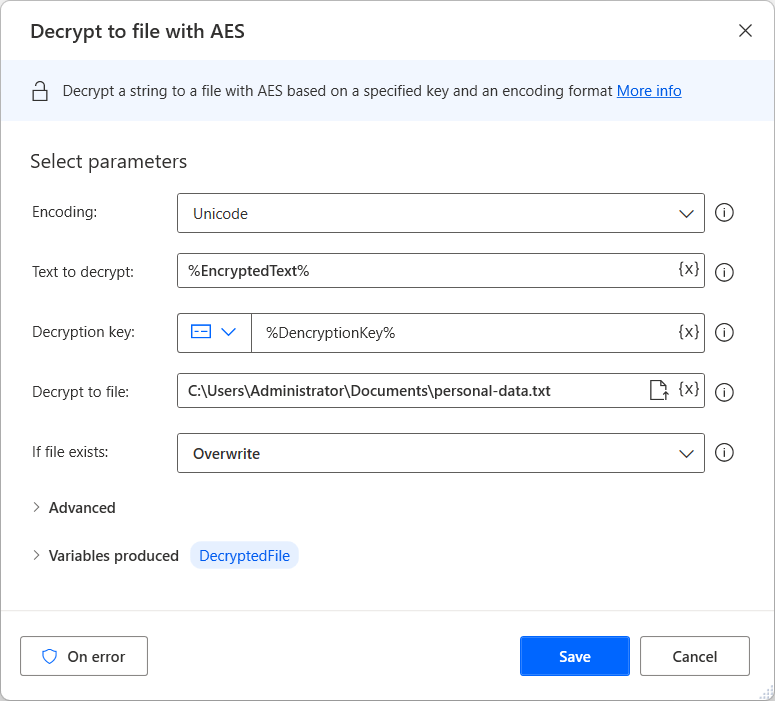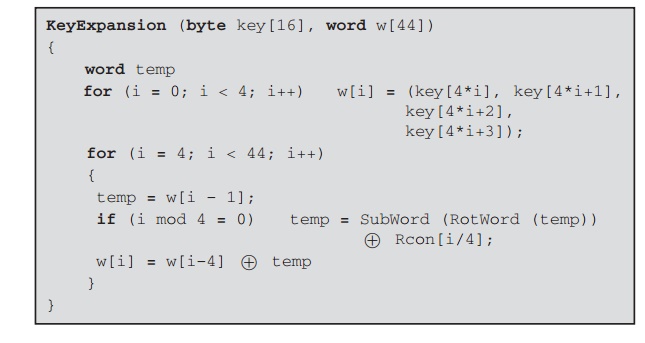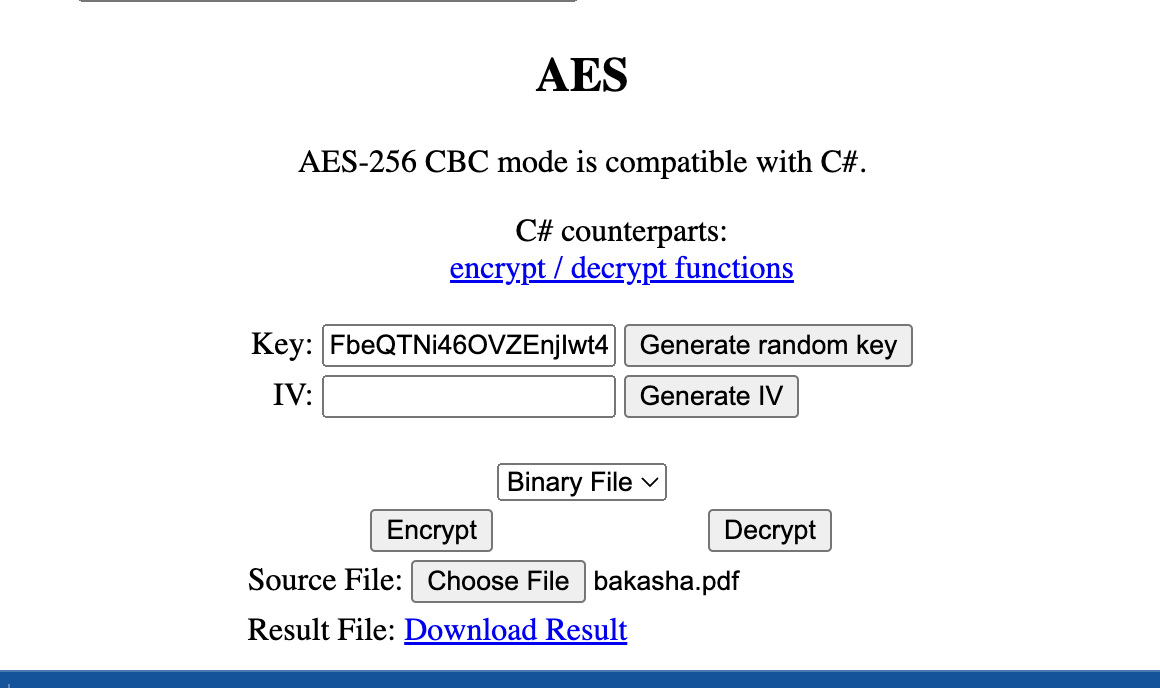
A Free And Easy C#-compatible Encryption Tool for Javascript | by Adam Fisher / fisher king (@therightstuff) | Level Up Coding
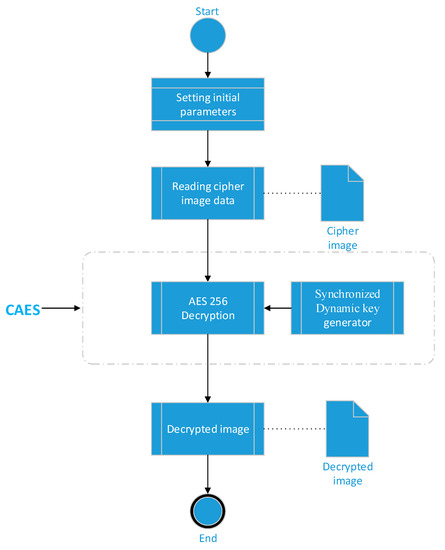
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm | HTML

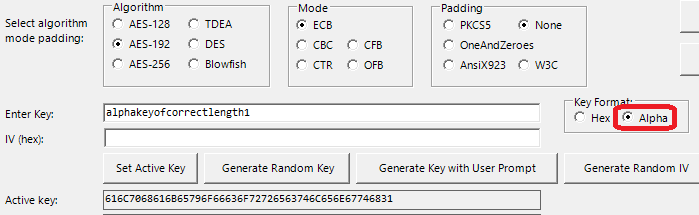
How to implement plain AES-128 encryption while packaging for HLS? · Issue #776 · shaka-project/shaka-packager · GitHub

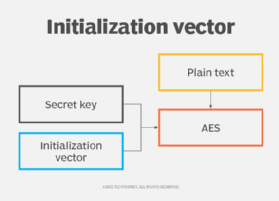
encryption - When using AES and CBC, is it necessary to keep the IV secret? - Information Security Stack Exchange